230,218 downloads Updated: September 17, 2020 Freeware. Review Free Download specifications 100% CLEAN report malware. Fast web browser that provides macOS users with a minimalist interface and a fast website rendering engine for browsing the Internet as effortlessly as. Contains a fix for an issue that could affect website usability when running Safari in 32-bit mode; other stability improvements. 5.1.6 534.56.5 Mac OS X v10.7: May 9, 2012 Bundled with Mac OS X v10.7.4, contains stability improvements. 5.1.7 534.57.2 Mac OS X v10.6 - 10.7: May 9, 2012. Music, TV, and podcasts take center stage. ITunes forever changed the way people experienced. Get the latest version of Safari for your Mac. Featured topics. About pop-up ads and windows in Safari. Learn how to block pop-up windows and handle persistent ads on your iPhone, iPad, iPod touch, or Mac. Intelligent Tracking in macOS. Safari now uses machine learning to identify advertisers and others who track your online.
Safari User Guide
You can change options in Safari preferences so that Safari always accepts or always blocks cookies and website data.

In the Safari app on your Mac, choose Safari > Preferences, click Privacy, then do any of the following:
Safari Version 9 For Mac
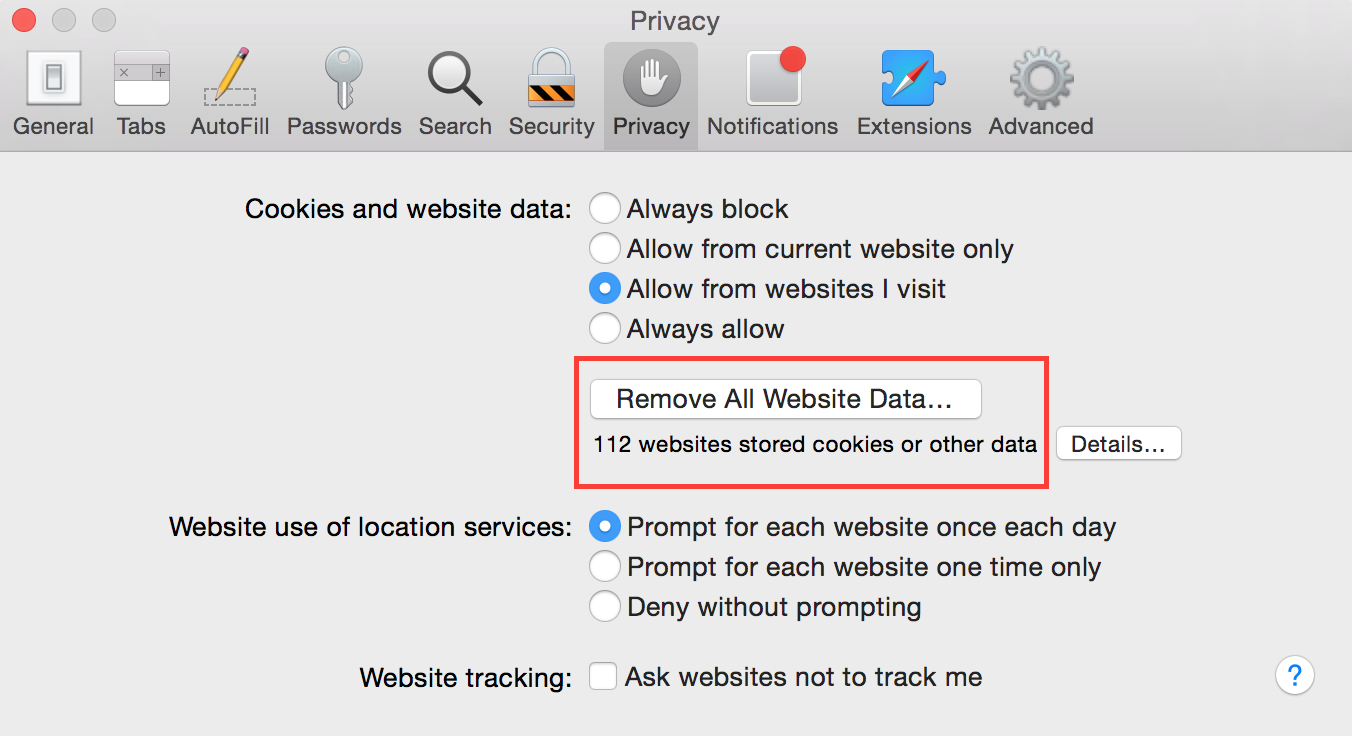
Prevent trackers from using cookies and website data to track you: Select “Prevent cross-site tracking.”
Cookies and website data are deleted unless you visit and interact with the trackers’ websites.
Always block cookies: Select “Block all cookies.”
Websites, third parties, and advertisers can’t store cookies and other data on your Mac. This may prevent some websites from working properly.
Always allow cookies: Deselect “Block all cookies.”
Websites, third parties, and advertisers can store cookies and other data on your Mac.
Remove stored cookies and data: Click Manage Website Data, select one or more websites, then click Remove or Remove All.
Removing the data may reduce tracking, but may also log you out of websites or change website behavior.
See which websites store cookies or data: Click Manage Website Data.
Note: Changing your cookie preferences or removing cookies and website data in Safari may change or remove them in other apps.
For the protection of our customers, Apple does not disclose, discuss, or confirm security issues until a full investigation has occurred and any necessary patches or releases are available. To learn more about Apple Product Security, see the Apple Product Security website.
For information about the Apple Product Security PGP Key, see How to use the Apple Product Security PGP Key.
Where possible, CVE IDs are used to reference the vulnerabilities for further information.
To learn about other security updates, see Apple security updates.
Safari 9
Safari 9 For Mac Download
Safari
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: Visiting a malicious website may lead to user interface spoofing
Description: Multiple user interface inconsistencies may have allowed a malicious website to display an arbitrary URL. These issues were addressed through improved URL display logic.
CVE-ID
CVE-2015-5764 : Antonio Sanso (@asanso) of Adobe
CVE-2015-5765 : Ron Masas
CVE-2015-5767 : Krystian Kloskowski via Secunia, Masato Kinugawa
Safari Downloads
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: LaunchServices' quarantine history may reveal browsing history
Description: Access to LaunchServices' quarantine history may have revealed browsing history based on file downloads. This issue was addressed through improved deletion of quarantine history.
Safari Extensions
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: Local communication between Safari extensions and companion apps may be compromised
Description: The local communication between Safari extensions such as password managers and their native companion apps could be comprised by another native app. This issue was addressed through a new, authenticated communications channel between Safari extensions and companion apps.
Safari Extensions
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: Safari extensions may be replaced on disk
Description: A validated, user-installed Safari extension could be replaced on disk without prompting the user. This issue was addressed by improved validation of extensions.
CVE-ID
CVE-2015-5780 : Ben Toms of macmule.com
Safari Safe Browsing
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: Navigating to the IP address of a known malicious website may not trigger a security warning
Description: Safari's Safe Browsing feature did not warn users when visiting known malicious websites by their IP addresses. The issue was addressed through improved malicious site detection.
Rahul M (@rahulmfg) of TagsDock
WebKit
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: Partially loaded images may exfiltrate data across origins
Description: A race condition existed in validation of image origins. This issue was addressed by improved validation of resource origins.
CVE-ID
CVE-2015-5788 : Apple
WebKit
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: Visiting a maliciously crafted website may lead to an unexpected application termination or arbitrary code execution
Description: Multiple memory corruption issues existed in WebKit. These issues were addressed through improved memory handling.
CVE-ID
CVE-2015-5789 : Apple
CVE-2015-5790 : Apple
CVE-2015-5791 : Apple
CVE-2015-5792 : Apple
CVE-2015-5793 : Apple
CVE-2015-5794 : Apple
CVE-2015-5795 : Apple
CVE-2015-5796 : Apple
CVE-2015-5797 : Apple
CVE-2015-5798 : Apple
CVE-2015-5799 : Apple
CVE-2015-5800 : Apple
CVE-2015-5801 : Apple
CVE-2015-5802 : Apple
CVE-2015-5803 : Apple
CVE-2015-5804 : Apple
CVE-2015-5805
CVE-2015-5806 : Apple
CVE-2015-5807 : Apple
CVE-2015-5808 : Joe Vennix
CVE-2015-5809 : Apple
CVE-2015-5810 : Apple
CVE-2015-5811 : Apple
CVE-2015-5812 : Apple
CVE-2015-5813 : Apple
CVE-2015-5814 : Apple
CVE-2015-5815 : Apple
CVE-2015-5816 : Apple
CVE-2015-5817 : Apple
CVE-2015-5818 : Apple
CVE-2015-5819 : Apple
CVE-2015-5821 : Apple
CVE-2015-5822 : Mark S. Miller of Google
CVE-2015-5823 : Apple
WebKit
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: An attacker may be able to create unintended cookies for a website
Description: WebKit would accept multiple cookies to be set in the document.cookie API. This issue was addressed through improved parsing.
CVE-ID
CVE-2015-3801 : Erling Ellingsen of Facebook
WebKit
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: The Performance API may allow a malicious website to leak browsing history, network activity, and mouse movements
Description: WebKit's Performance API could have allowed a malicious website to leak browsing history, network activity, and mouse movements by measuring time. This issue was addressed by limiting time resolution.
CVE-ID
CVE-2015-5825 : Yossi Oren et al. of Columbia University's Network Security Lab
WebKit
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: Visiting a malicious website may lead to unintended dialing
Description: An issue existed in handling of tel://, facetime://, and facetime-audio:// URLs. This issue was addressed through improved URL handling.
CVE-ID
CVE-2015-5820 : Guillaume Ross, Andrei Neculaesei
WebKit CSS
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: A malicious website may exfiltrate data cross-origin
Description: Safari allowed cross-origin stylesheets to be loaded with non-CSS MIME types which could be used for cross-origin data exfiltration. This issue was addressed by limiting MIME types for cross-origin stylesheets.
CVE-ID
CVE-2015-5826 : filedescriptior, Chris Evans
WebKit JavaScript Bindings
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: Object references may be leaked between isolated origins on custom events, message events and pop state events
Description: An object leak issue broke the isolation boundary between origins. This issue was addressed through improved isolation between origins.
CVE-ID
CVE-2015-5827 : Gildas
WebKit Page Loading
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: WebSockets may bypass mixed content policy enforcement
Description: An insufficient policy enforcement issue allowed WebSockets to load mixed content. This issue was addressed by extending mixed content policy enforcement to WebSockets.
Kevin G. Jones of Higher Logic
WebKit Plug-ins
Available for: OS X Mavericks v10.9.5, OS X Yosemite v10.10.5 and OS X El Capitan v10.11
Impact: Safari plugins may send an HTTP request without knowing the request was redirected
Description: The Safari plugins API did not communicate to plugins that a server-side redirect had happened. This could lead to unauthorized requests. This issue was addressed through improved API support.
CVE-ID
CVE-2015-5828 : Lorenzo Fontana
Safari 9 For Mac
FaceTime is not available in all countries or regions.
